[Update 2021-12-18: See this post for a better solution.]
Some ideas are just too silly to not try and follow through with.
Earlier this evening, Michael Tsai tweeted
Safari is already less compatible, so if the user interface is going to be worse, too, I just don’t see the point. The main other thing keeping me there is 2FA auto-fill.
and I replied
I’m very, very close to writing a KeyboardMaestro macro to grab the latest 2FA code from Messages.app to work around this.
I was mostly joking.
Until I thought, why not?
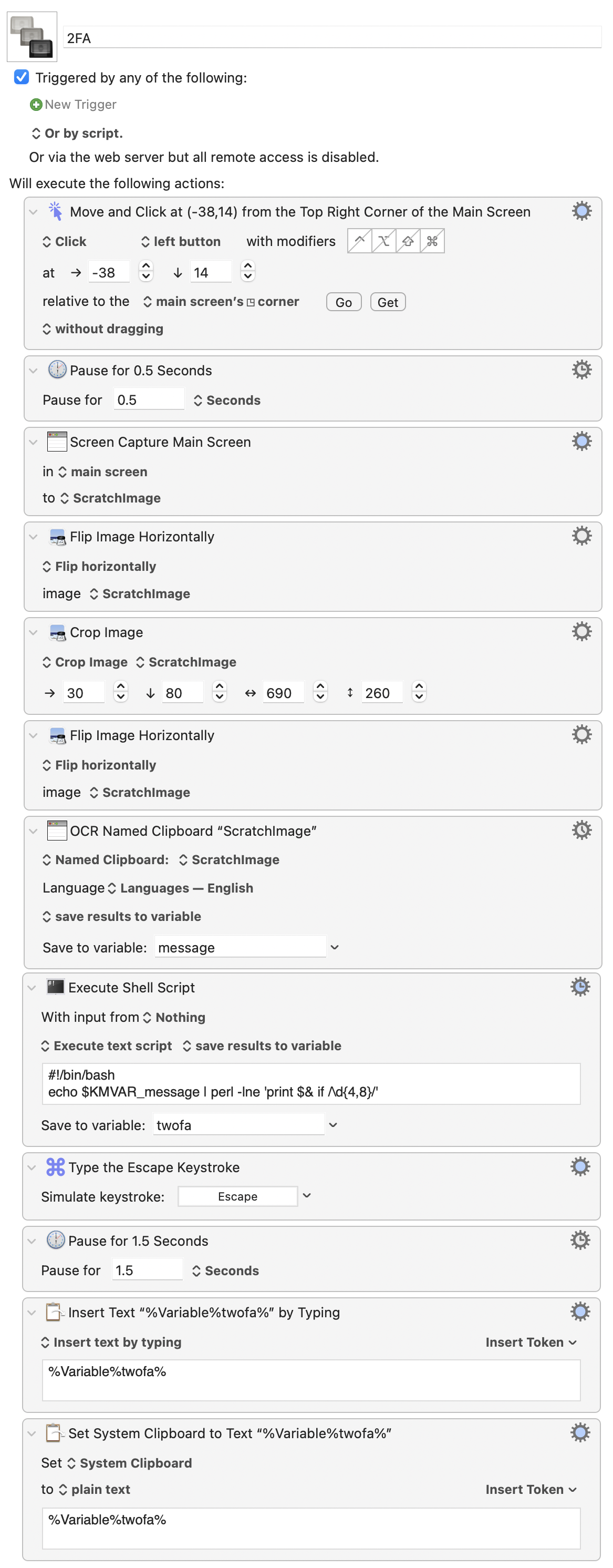
Here it is. Just launch the macro, and it grabs the new two-factor code that was just texted to you. Then inserts it into your non-Safari browser.
And here’s how it works…
My first instinct was to try and copy the text of the most recent conversation in Messages.app and then pipe that through a regular expression to parse out the two-factor code.
For very boring reasons that aren’t very interesting, I’ll just say that I spent two days a few years ago trying to hack together something similar using Messages’ AppleScript interface. It wasn’t very good back then, so I didn’t even attempt going down that road tonight – especially since it’s a Catalyst app now.
Instead, I decided to just try “clicking” my way through the UI with KeyboardMaestro. Something along the lines of…
- Activate Messages.app
- Click a known x,y coordinate from the top-left corner of the window to select the first non-favorite conversation.
- Double-click a known x,y coordinate from the bottom-left corner of the window to select a word in the last message of that conversation.
- Type ⌘A to select all the text in that message.
- ⌘C to put it on the clipboard.
- Parse out the code.
- Paste the code onto the clipboard to use.
That sort of worked. But it wasn’t very reliable. Mostly because Messages.app takes so long to wake up sometimes. If its window hasn’t been displayed in a while, it can take a not-insignificant amount of time to appear. And then switching to the newest conversation is similarly slow.
As much as I tried to work around this by adding delays in the UI script or other KeyboardMaestro tricks, it was too fragile to be reliable in my testing. I needed another approach.
Here’s what ended up working.
- Click the menubar’s clock to activate Notification Center. (By the way, it took me a full damn month after installing Big Sur before I realized what Apple had done with the Notification Center icon and that it was still accessible without needing to use the two-finger-swipe-from-right trackpad gesture.)
- Wait for the reveal animation to finish.
- Take a screenshot.
- Flip the image horizontally. (Because KM’s crop action only works from the top-left corner of an image.)
- Crop out the known size/position of the first notification message. (All message bubbles are the same size no matter their contents.)
- Flip the image horizontally (back to the original orientation).
- OCR the text contained in that cropped image, which should hopefully contain our two-factor code.
- Extract the code using a shell script. (Please dear god Apple don’t remove Perl from Monterey.)
- Close Notification Center.
- Wait for the collapse animation to finish. (This delay is longer because I found I had to wait for the animation to finish and then an additional delay for the active application to regain keyboard focus a moment later.)
- Type the code into the current app (probably your non-Safari browser).
- Put the code on the clipboard for good measure.
And, boom, in just twelve easy steps… ?♀️
You can download the macro here.
Caveats
- I haven’t tested this yet on multi-monitor systems.
- The image crop dimensions assume you’re using a retina display.
- The regular expression will probably fail for you, but it works for Google and my bank.
- This is all a dumb hack that isn’t actually meant to be taken seriously but illustrates the internet’s collective knee-jerk response to not wanting to use the new Safari.
Comments are closed.